Cisco’s Encrypted Traffic Analytics (ETA), a software platform that monitors network packet metadata to detect malicious traffic, even if its encrypted, is now generally available.
The company initially launched ETA in June, 2017 during the launch of its intent-based network strategy and it’s been in a private preview since then. Today Cisco rolled ETA out beyond just the enterprises switches it was originally designed for and made it available on current and previous generation data center network hardware too.
+MORE AT NETWORK WORLD: What is intent based networking? | Why intent based networking could be a big deal +
 Cisco
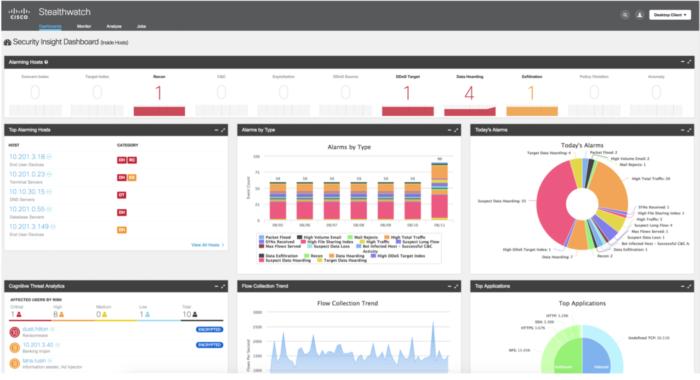
CiscoCisco’s Encrypted Traffic Analytics uses a software named Stealthwatch to compare the metadata of benign and malicious network packets to identified malicious traffic, even if its encrypted.
What ETA is
Encrypted Traffic Analytics is a product deployed on customers’ premises that monitors their network and collects information about traffic flows. It uses a series of sensors placed throughout the network to screen all traffic traversing through it. ETA uses a combination of local analysis engines combined with a cloud-based platform that analyzes anonymized metadata about network traffic to search for and block malicious traffic, even if it’s encrypted.
Cisco launched ETA during its intent based networking (IBN) strategy rollout because it uses some of the advanced software the company developed for IBN, including machine learning components that evolve to protect against changing vulnerabilities.
How ETA works
ETA collects metadata about traffic flows using a modified version of NetFlow and searches for characteristics that indicate the traffic could be malicious. It inspects the initial data packet, which is translated in the clear, even in encrypted traffic. It also records the size, shape and sequence of packets, how long they take to traverse the network, and it monitors for other suspicious characteristics such as a self-signed certificate, or whether it has command-and-control identifiers on it.
All of this data can be collected on traffic, even if its encrypted. “ETA uses network visibility and multi-layer machine learning to look for observable differences between benign and malware traffic,” Cisco explains in a blog post announcing ETA.
If characteristics of malicious traffic are identified in any packets, they are flagged for further ianalysis through deep packet inspection and potential blocking by an existing security appliance like a firewall.
ETA’s monitoring system is named StealthWatch and the cloud-based data store is named Talos. Meanwhile, if traffic is identified as malicious, ETA can report it to Cisco’s DNA Center network management software to ensure that traffic is blocked throughout the entire network. Cisco says its using machine learning algorithms to train ETA to search for new vulnerabilities and adapt to changing ones.
“When you’re doing security, the more visibility the better,” explains Scott Harrell, Cisco senior vice president and general manager of enterprise networking. “You want to have a huge wealth of data, not just about what’s happening in real-time, but what’s happened historically. A lot of times in security, there is smoke before you know there is fire.”
If potentially malicious traffic has been identified, information such as which host initiated the conversation and what information was exchanged are important to determine the scope of a problem, Harrell says.
Why ETA could be a big deal
More and more traffic is encrypted. Cisco estimates 55% of traffic on the web is encrypted now, a figure that Gartner predicts will grow to 80% by 2019. Meanwhile, up to 41% of hackers use encryption to evade detection, Cisco says.
Organizations use a range of options for ensuring the security of encrypted traffic in their networks. Most of these approaches use next-generation firewalls, deep packet inspection (DPI) or Secure Socket Layer (SSL) inspection. Harrell says these tools require some sort of tradeoff though. SSL inspection, for example, intercepts and decrypts traffic to determine if it is malicious and only after it’s confirmed to be safe will complete the connection. Malware can infect that SSL inspection, leaving it vulnerable. Harell argues that its inefficient to decrypt all traffic, then re-encrypt it before allowing users to access it. Cisco says it is the first company to have developed a way to monitor encrypted traffic for vulnerabilities.
IoT security
Harell says ETA could be important in the world of IoT, too. ETA’s ability to monitor encrypted traffic’s metadata means it could analyze all IoT traffic without necessarily needing to put security tools like firewalls on each of the small-form-factor IoT devices.
Cisco says ETA has another benefit: cryptographic compliance. Some organizations are required to use certain levels of encryption for regulatory reasons. ETA, through its use of analysis metadata, can provide proof of certain levels and types of encryption being used.
How to buy ETA
ETA is generally available as of today and is available across data center, campus and branch office hardware, including the Catalyst 9000 switching line, as well as previous and current generation Integrated Services Router (ISR), as well as Aggregation Services Router (ASR) and the Cloud Services Router (CSR). ETA is included in purchases of these hardware devices along with a subscription to Cisco ONE software that includes Stealthwatch.



